Les drones peuvent-ils être piratés, suivis et utilisés pour transporter des passagers ? | Digi International

Les drones peuvent-ils être piratés, suivis et utilisés pour transporter des passagers ? | Digi International

DroneSec, a private intelligence agency for drone threats, that provides UAS Threat Intelligence and drone security training - Space & Cybersecurity Info

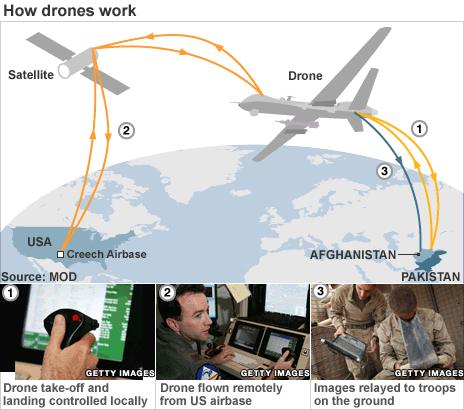
US and UK hacked Israeli drones, fighter jets in "Anarchist" operation to spy on military operations in Middle East - CBS News

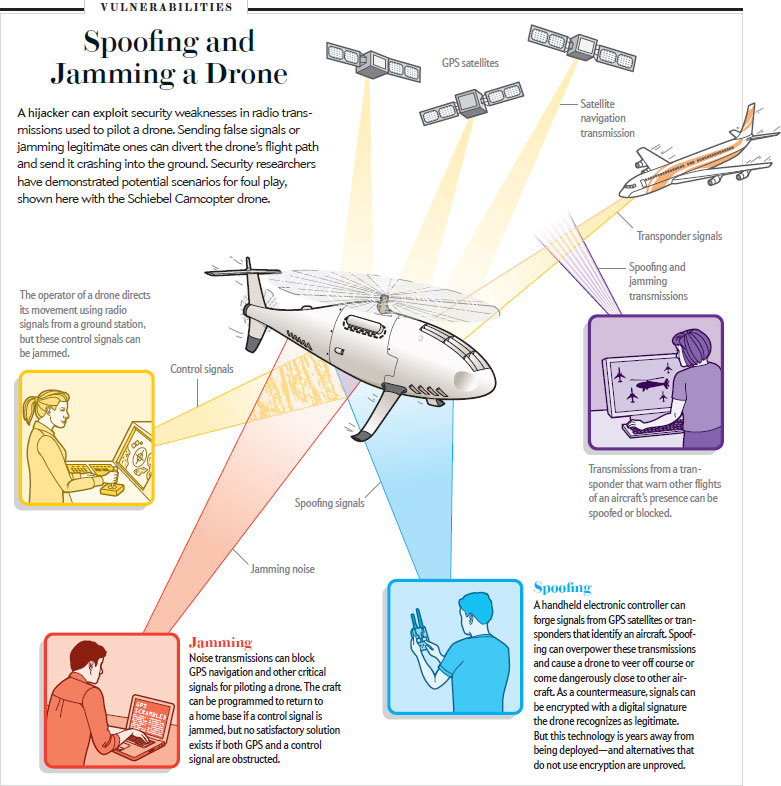
Black Hat Demos Attacks on IoT, Bad Protocols, and Drones - Nachrichten zum Thema Sicherheit - Trend Micro DE
/cdn.vox-cdn.com/uploads/chorus_asset/file/7744711/617471794.jpg)